Leveraging Wazuh for Compliance with Bank Indonesia and OJK Cybersecurity Regulation (Part 1)

As cyber threats continue to evolve in complexity and impact, Bank Indonesia and the Financial Services Authority (OJK) have issued updated regulatory frameworks to enhance the security posture and operational resilience of entities in the financial sector.
Hi, I’m Ismail — CEO of Cyberkarta, one of the fastest-growing cybersecurity companies in Indonesia. If you have ideas, insights, or challenges in cybersecurity that you’d like to explore together, feel free to reach out through the comments or connect with me on LinkedIn. I’d love to hear from you and collaborate on building a safer and more resilient digital ecosystem.
LinkedIn Profile — https://www.linkedin.com/in/ismail-hakim/
Company Website — https://cyberkarta.com
Introduction
Bank Indonesia, as the central bank of the Republic of Indonesia, is responsible for maintaining monetary stability, payment system security, and financial system resilience. It regulates cybersecurity for payment systems and financial market players through:
- PBI No. 2 of 2024 on Cybersecurity and Information System Resilience,
- PADG No. 24 of 2024 as the implementing technical guideline for PBI 2/2024.
Otoritas Jasa Keuangan (OJK) is the Financial Services Authority of Indonesia, overseeing financial institutions such as banks, insurance companies, and fintech entities. It provides regulatory guidance on IT risk and innovation through:
- POJK No. 11/03/2022 on the Information Technology Provider for Banking Industry,
- SEOJK No. 21/MRTI as the implementing circular of POJK 11/03/2022,
- SEOJK No. 29/SEOJK.03/2022 on Risk Management in the Use of Information Technology by Commercial Banks.
These regulations require financial institutions, payment system operators, and other regulated entities to:
- Establish strong cybersecurity governance,
- Identify and mitigate cyber risks,
- Detect and respond to cyber incidents effectively,
- Maintain maturity in cybersecurity practices,
- Report incident and maturity assessments in strict formats and timelines,
- Demonstrate compliance and audit readiness.
Wazuh, an open-source Security Information and Event Management (SIEM) solution, offers a comprehensive suite of features that can support financial institutions in meeting these obligations, including:
- Real-time threat detection and correlation
- File Integrity Monitoring (FIM)
- Centralized log collection and secure storage
- Auditd-based activity monitoring
- Vulnerability detection
- Custom rule creation for regulation-specific monitoring
- Automated incident response and alerting
In this blogpost, we will explore how Wazuh can help your organization align with Indonesia’s most up-to-date cybersecurity and IT governance regulations — PBI 2/2024, PADG 24/2024, POJK 11/03/2022, SEOJK 21/MRTI, and SEOJK 29/SEOJK.03/2022 — through concrete use cases and compliance mappings.
Understanding the Regulations
To effectively build a compliant and secure infrastructure, financial institutions in Indonesia must first understand the scope and intent of the prevailing regulations issued by Bank Indonesia and Otoritas Jasa Keuangan (OJK). These regulations establish a standardized framework to govern cybersecurity risk, operational resilience, incident response, and auditability in the financial sector.

Bank Indonesia Regulations
- PBI No. 2 of 2024 — Cybersecurity and Information System Resilience
- Focuses on protecting confidentiality, integrity, and availability of financial systems and data.
- Covers governance, prevention, detection, response, and recovery from cyber incidents.
- Requires reporting cyber incidents within 1 hour (initial notification) and full reporting within 3 calendar days.
- Applies to payment system operators, financial market players, and supporting institutions.
PBI No. 2 of 2024 emphasizes:
- Cyber incident prevention (identification, protection, detection)
- Response and recovery readiness
- Logging and documentation of incidents
- Periodic maturity assessments
2. PADG No. 24 of 2024 — Technical Guideline for PBI 2/2024
- Serves as the implementation framework for PBI 2/2024.
- Details operational procedures, reporting templates, incident classification, and technical assessments.
- Outlines periodic reporting (e.g., annual cybersecurity maturity assessments).
- Requires technical controls such as:
- Continuous monitoring and alerting
- Incident logging and forensic support
- Response workflows with reporting structures
OJK Regulations
1. POJK No. 11/03/2022 — Information Technology Provider for Banking Industry
- Requires integration of IT risk into enterprise-wide risk management.
- Covers system development, operations, third-party risk, data protection, and continuity planning.
POJK No. 11/03/2022 mandates:
- Secure logging and monitoring of IT infrastructure
- Regular internal/external IT audits
- Risk-based access control and configuration management
2. SEOJK No. 21/SEOJK.03/2017 (MRTI) — IT Risk Management for Financial Institutions
- Provides technical instructions on how to apply several controls in POJK 11/03/2022.
SEOJK No. 21/SEOJK.03/2017 (MRTI) emphasizes:
- Early risk identification and real-time threat detection
- Vendor risk monitoring
- Backup and disaster recovery planning
3. SEOJK No. 29/SEOJK.03/2022 — Cybersecurity and Information System Resilience
- Tailored specifically for commercial banks under OJK supervision.
- Clarifies roles of IT Steering Committees and CISO.
SEOJK No. 29/SEOJK.03/2022 Emphasizes:
- Centralized logging and secure storage
- Continuous system monitoring
- Cyber incident readiness and rapid response coordination
Regulation-to-Capability Mapping
These mappings illustrate how Wazuh can directly support compliance with BI and OJK mandates, helping institutions simplify regulatory alignment through automated controls and audit-ready features.
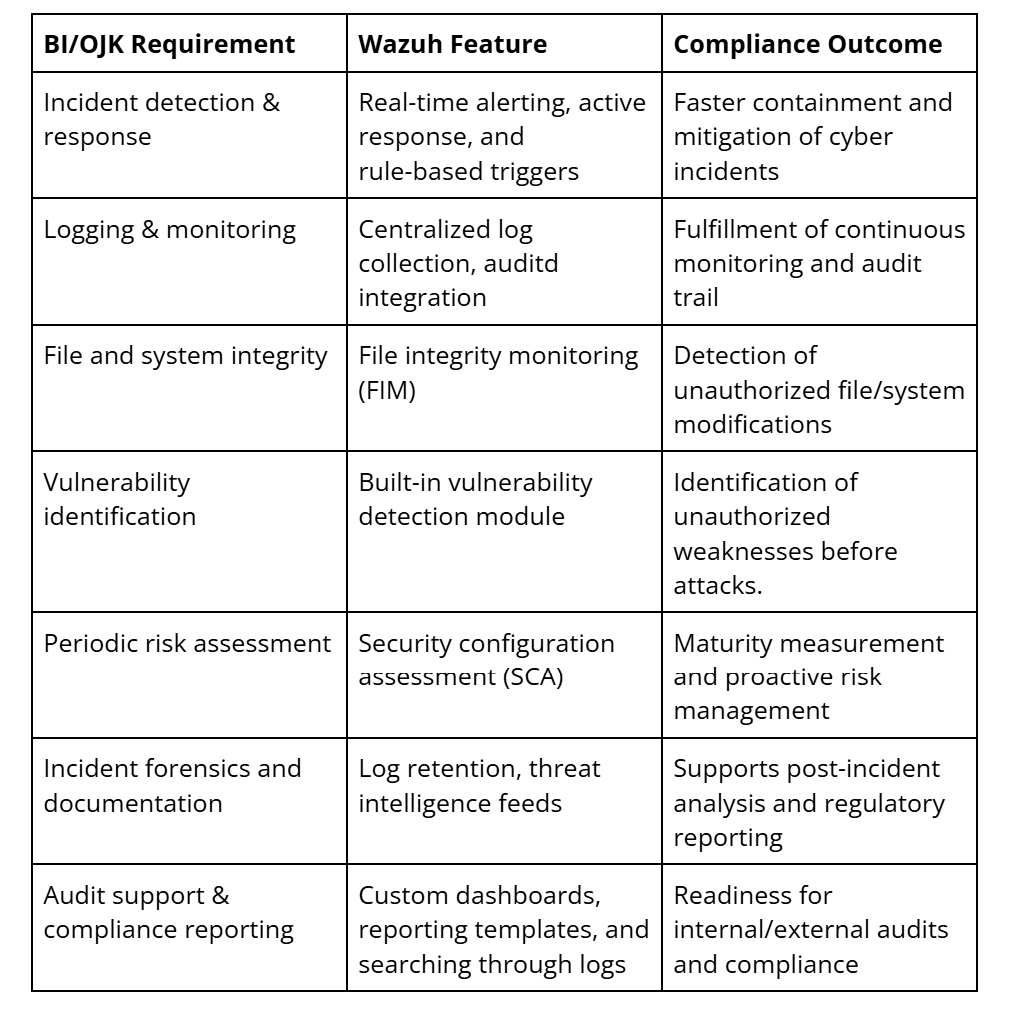
Supporting BCP/DRP (Business Continuity Planning / Disaster Recovery Planning)
Wazuh plays a strategic role in supporting BCP and DRP initiatives by enabling:
- Real-Time Alerting: Helps organizations respond to early indicators of compromise or service disruption.
- System Audit Logs: Maintains a historical trail of events across systems to support root cause analysis and forensic investigation.
- Resource Usage Monitoring: Tracks system health and capacity, which is critical during failover or recovery scenarios.
- Custom Alert Rules: Detects key failures or anomalies that may impact the continuity of critical business services.
- Log Retention: Ensures access to security events and alerts before, during, and after incidents for DR documentation and evaluation.
These capabilities empower IT and cybersecurity teams to integrate Wazuh as part of their risk-based BCP/DRP plans, ensuring faster incident response and recovery coordination.
Enabling Data Classification and Information System Security (Klasifikasi Data dan Keamanan Sistem Informasi)
National standards emphasize the importance of protecting different classes of data based on sensitivity and business impact. Wazuh helps enforce and monitor data classification policies through:
- File Integrity Monitoring (FIM): Tracks changes to files containing classified or sensitive data.
- Access Monitoring: Identifies unauthorized access attempts to sensitive directories or databases.
- Auditd and Sysmon Integration: Enables visibility into user actions, process execution, and access logs.
- Custom Decoders and Rules: Tailor detection to match the organization’s classification scheme and sensitivity levels.
- Security Configuration Assessment (SCA): Assesses compliance of endpoints and servers with hardening policies.
By aligning Wazuh’s monitoring capabilities with internal data classification policies and information system controls, organizations can reinforce the confidentiality, integrity, and availability (CIA) of their critical assets.
Conclusion
As the cybersecurity landscape continues to grow more complex, financial institutions and payment system operators in Indonesia must proactively align with the regulatory expectations set forth by Bank Indonesia and OJK. The combination of PBI 2/2024, PADG 24/2024, POJK 11/03/2022, SEOJK 21/MRTI, and SEOJK 29/SEOJK.03/2022 provides a clear mandate for robust governance, technical controls, and operational resilience.
Wazuh, as a powerful and flexible open-source SIEM solution, offers the visibility, automation, and audit-readiness required to meet these demands. From real-time detection to vulnerability management, log centralization, and compliance reporting, Wazuh delivers actionable insights and operational assurance across all layers of security.
By integrating Wazuh into their cybersecurity architecture, institutions can not only ensure compliance but also strengthen their ability to detect threats, respond swiftly to incidents, and maintain business continuity under pressure.
In a regulatory environment that prioritizes maturity, accountability, and responsiveness, Wazuh is a strategic enabler of secure, compliant, and future-ready financial infrastructure in Indonesia.
💡 Coming Up Next: Real-World Examples
The next part of this blog series will focus on practical examples and use cases that illustrate how Wazuh can be applied in real operational environments. These scenarios will highlight the relevance of Wazuh’s capabilities in supporting day-to-day cybersecurity operations and regulatory compliance efforts within Indonesia’s financial sector.
Leveraging Wazuh for Compliance with Bank Indonesia and OJK Cybersecurity Regulation (Part 1) was originally published in Cyberkarta on Medium, where people are continuing the conversation by highlighting and responding to this story.